Table of contents
No headings in the article.
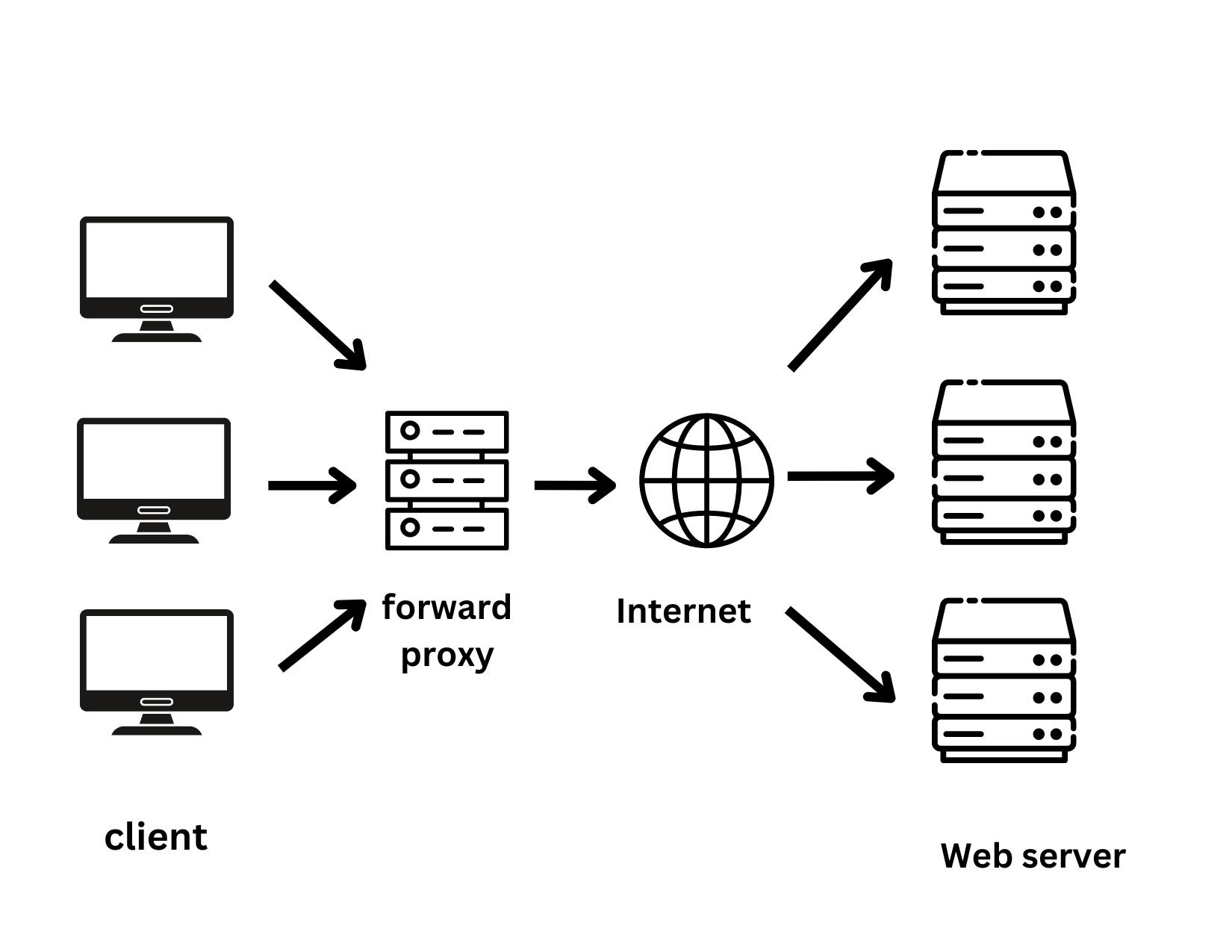
For network security, reverse proxies and forward proxies are essential. A forward proxy acts as an intermediary between a client and a server. When a client requests data from the server, it forwards the request to the server. The client cannot directly contact servers when using a forward proxy. Because it conceals the identity of the client, it is useful. Forward proxy servers hide the IP address of clients from the server. The forward proxy checks the validity of the request first. If the request is not authorized, it is blocked. It is used by many private networks, such as schools, universities, and banks, to secure their networks.
A transparent proxy is also an intermediary system that works between a client and a server and intercepts requests for caching, filtering, and gateway. Whenever a user makes a request, a transparent proxy saves a copy of the response that it receives from the server. The result is served to him when he needs it again. A transparent proxy prevents access to unauthorized services. It filters requests made by clients that may be harmful to it.
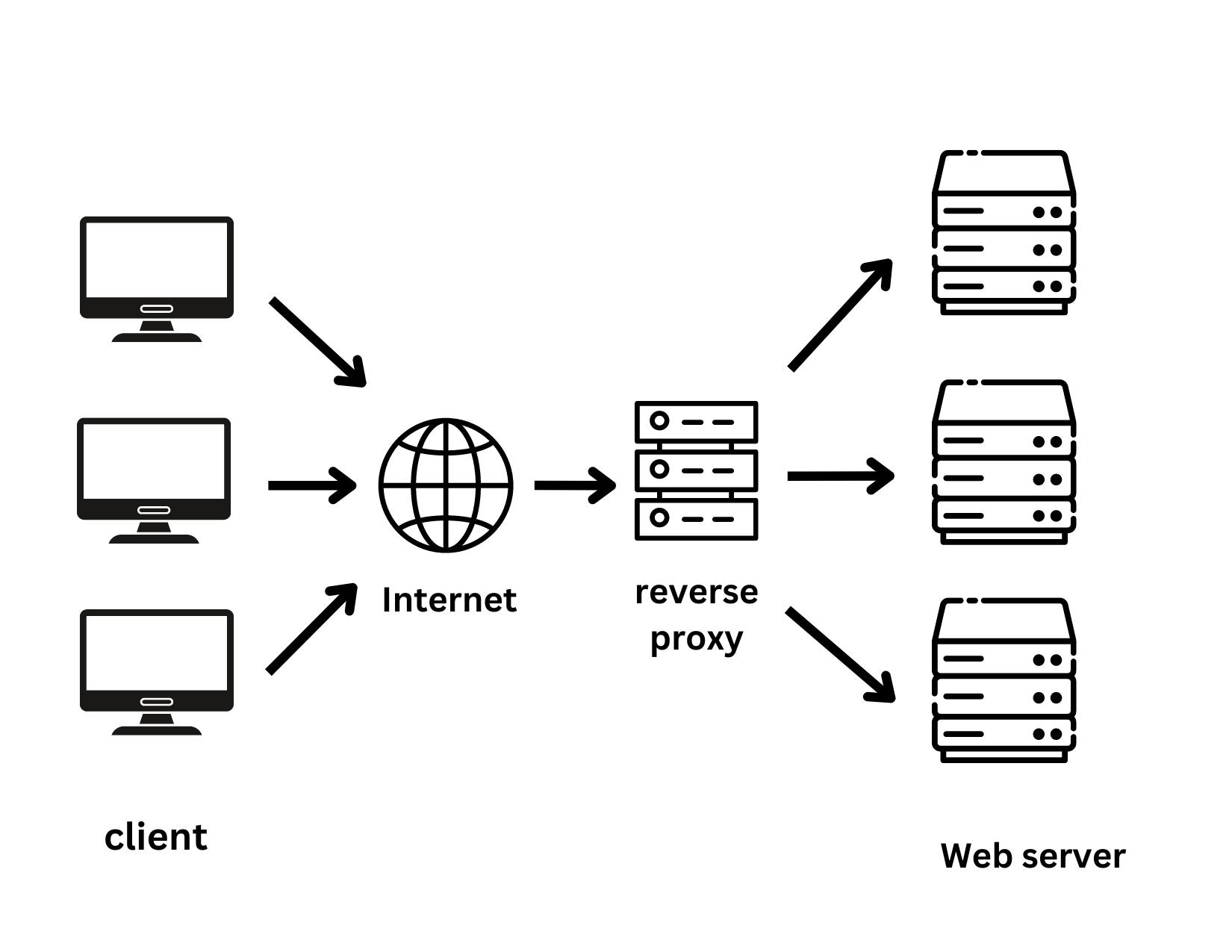
On the other hand, a reverse proxy sits in front of servers that accept client requests. It's similar to a forward proxy but the main difference is that it ensures that no client can directly make requests to the server. So the server's IP address is hidden from the client which prevents DDoS attacks. For handling requests, the reverse proxy uses Round-Robin
Reverse proxies are used for -
Load balancing - instead of managing all network traffic for a single server, this site distributes network traffic evenly across a pool of servers to handle the requests for the same site. This will prevent any single server from being overloaded with client requests.
Caching - A reverse proxy can cache the content of the request to reduce the load on the server.
Compressing - A reverse proxy can compress the content to optimize.
SSL Encryption - A reverse proxy can be configured to encrypt and decrypt SSL communications to secure requests and responses.