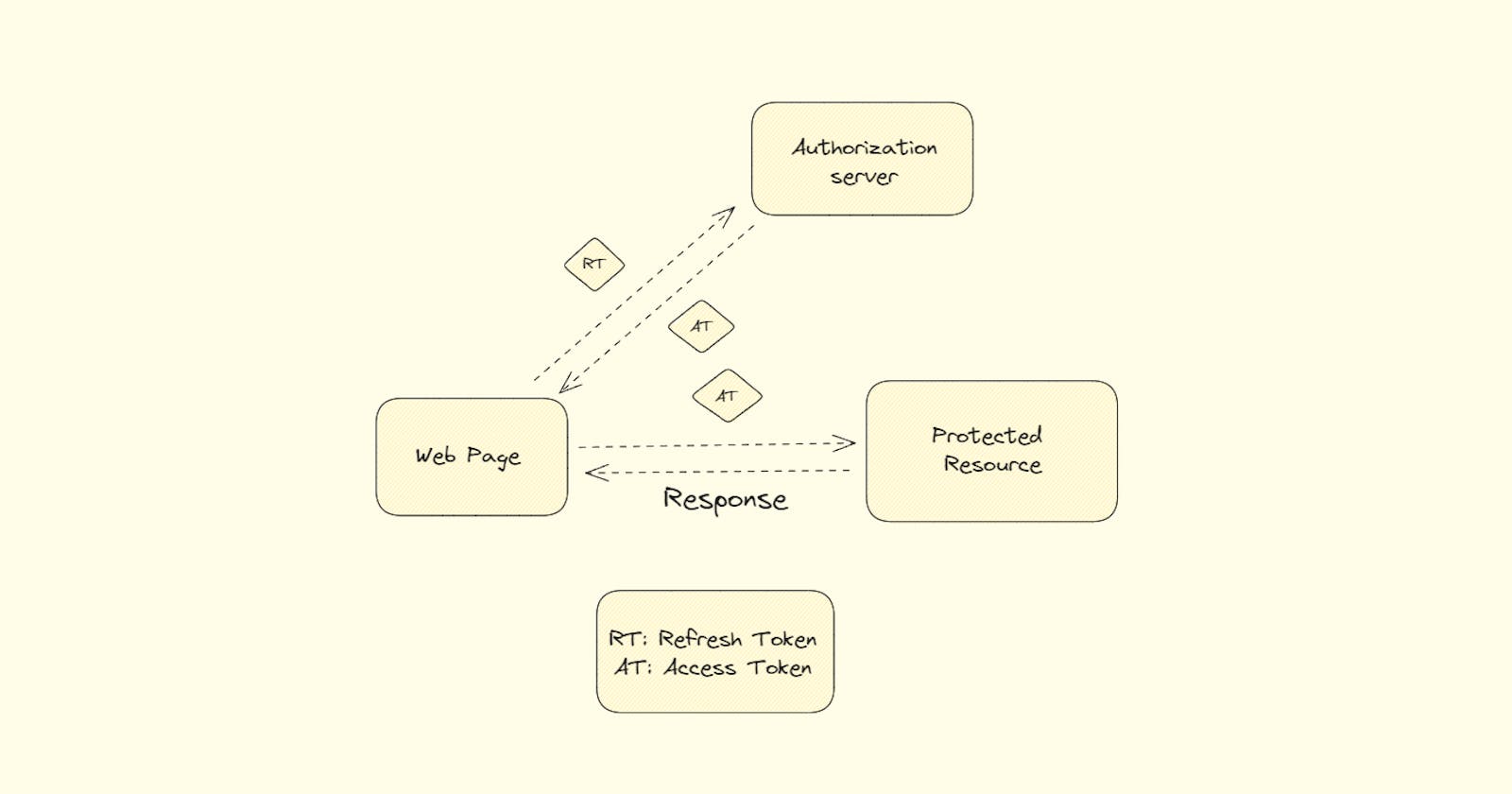
In the world of web applications, ensuring secure authorization and authentication is crucial. JSON Web Tokens (JWTs) have gained popularity as a means of securely transmitting information between parties. However, many developers overlook best practices, relying solely on access tokens stored in local storage. In this blog post, we will explore the pitfalls of this approach and discuss the advantages of incorporating refresh tokens, refresh token rotation, and reuse detection for a more robust and secure authentication system.
The Problem with Storing Access Tokens in Local Storage
Storing access tokens in local storage may seem convenient, but it poses significant security risks. Local storage is susceptible to cross-site scripting (XSS) attacks, which can allow malicious actors to gain access to sensitive data. Additionally, local storage lacks built-in protection against Cross-Site Request Forgery (CSRF) attacks, making your application vulnerable to unauthorized access.
Is the access token enough / what is the refresh token?
Refresh tokens are long-lived tokens used to obtain new access tokens after the initial authentication. With refresh tokens, users don't need to provide their credentials (username and password) every time they need a new access token. Instead, they present the refresh token, which is a shorter and less sensitive piece of information. This reduces the authentication overhead for both the user and the server. They have a longer expiration time and are stored securely on the server or in an HTTP-only cookie, mitigating the risks associated with local storage. By using refresh tokens, you can minimize the exposure of access tokens and enhance overall security. But using a refresh token only won't solve all the security threats.
Refresh Token Rotation
Refresh token rotation involves generating a new refresh token for each request to obtain a new access token. This practice adds a layer of security by invalidating the previously issued refresh token. In case a refresh token is compromised, the impact is limited, as the attacker will have a limited window to abuse it. Refresh token rotation also helps in detecting and mitigating potential unauthorized access attempts.
Reuse Token Detection
Token reuse detection is a mechanism to identify and prevent the misuse of refresh tokens. By maintaining a record of issued refresh tokens, you can track their usage and detect any unusual patterns. For example, if a refresh token is used simultaneously from different IP addresses or locations, it could indicate a potential security breach. By implementing token reuse detection, you can take proactive measures to block suspicious activities and protect your users' accounts.
Conclusion
When it comes to authentication and authorization in web applications, it is crucial to prioritize security. Storing access tokens in local storage can leave your application vulnerable to attacks. By incorporating refresh tokens, refresh token rotation and token reuse detection, you can significantly enhance the security of your system. Implementing these best practices will help protect your users' sensitive information and ensure a more robust authentication process. Rotating refresh tokens and Token reuse detection may not eliminate the risk, but it can reduce it to a certain extent.
Remember, security is an ongoing effort, and it's essential to stay up-to-date with the latest industry standards and recommendations. By following the guidelines discussed in this blog, you can take a significant step toward building a secure and reliable authentication system for your application.